3.5 – Users
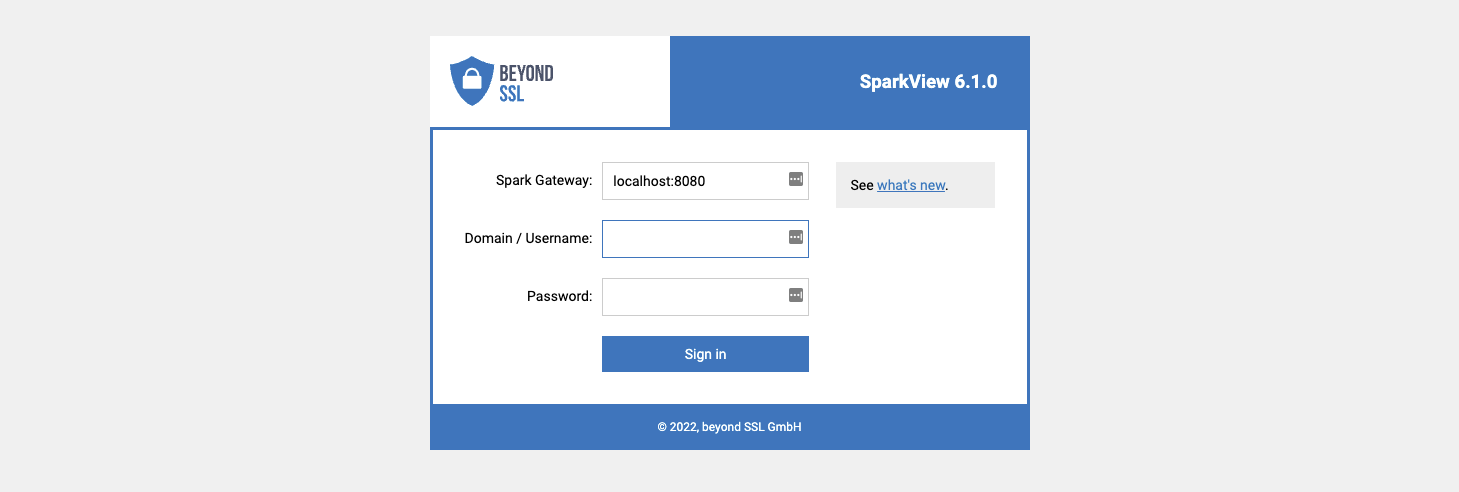
You can use users.json file to configure: users (name and password), RDP hosts (configured in servers.json) a user can access. User will have to log in when this file was used (starting from login.html)
You can also log in with Google, Yahoo account etc with OAuth 2 integration. For OAuth integration
- You don’t need to enter user name and password in the login.html.
- Make sure the user name in users.json is your email address (Gmail address if you are using Google Account).
- The password in users.json will be ignored, so you can give any passwords to user.
If you don’t need this OAuth integration, you can remove following part from login.html:<a href="/OPENID?id=Google"><img src="google.png" title="Sign in with Google account"/></a>
Please check Chapter 3.22 for more information about OAuth 2.
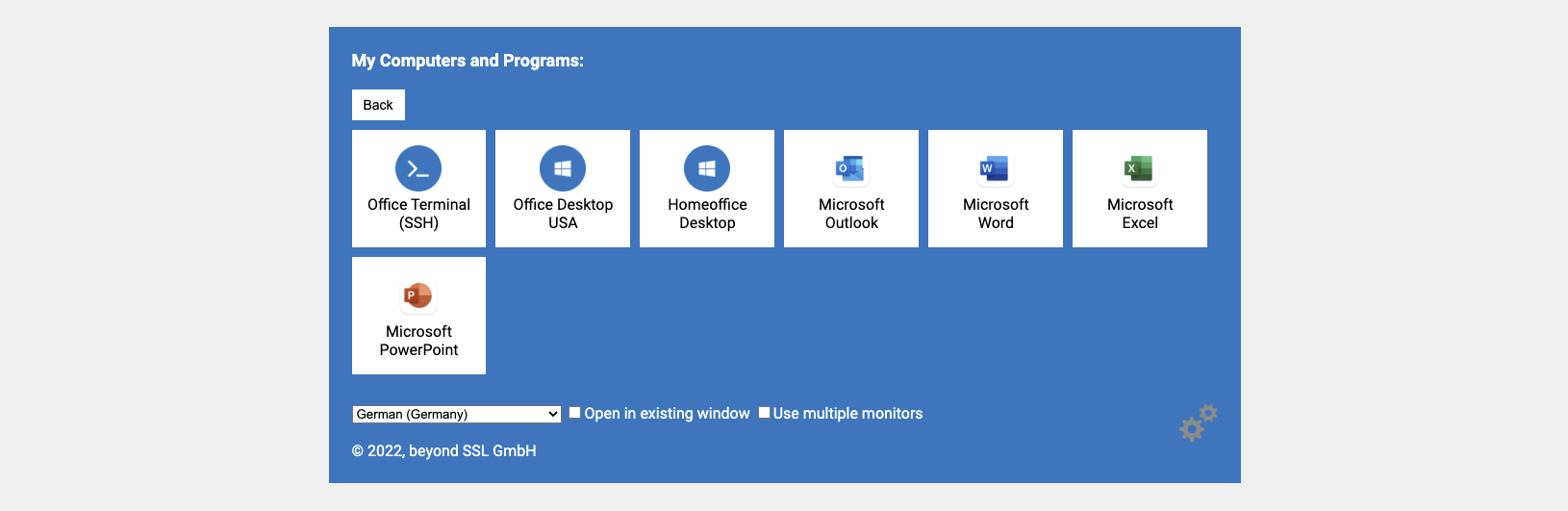
User will see a list of RDP hosts and applications they can use after logging in:
You can also use config.html to configure users.json. Use your browser and navigate to: http://localhost/config.html. For security reason, this page can be only accessed from localhost. The user name should be your email if you are using OpenID integration (log in with Google Account etc).
The following parameters can be stored when creating a user:
- Name
- Password
- Server, which the user is allowed to access
- Domain user (yes/no)
- Domain server
- Transfer credentials to connection
- Host name (for RDP connections)
You can import users from Active Directory too. These domain users will use active directory authentication and don’t need to have passwords (default is ***).
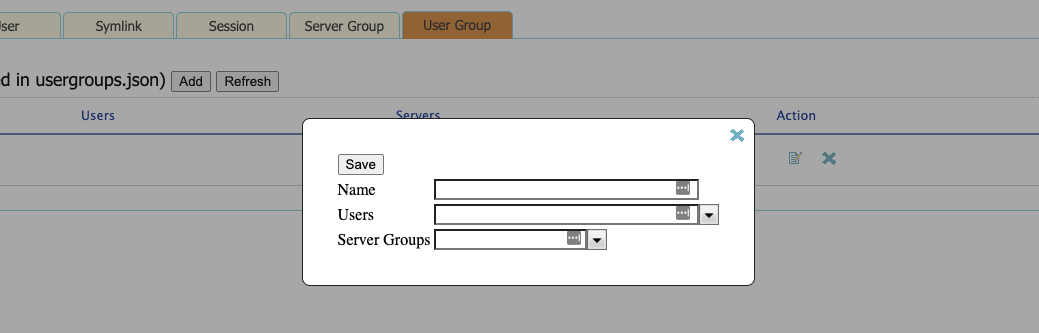
You can also configure user group, which is saved in userGroups.json by default:
An authenticator app (e.g. Google Two-
Activate two-factor authentication
withorAuthenticator) Microsoftis Authenticator:
- Set
twoFAtwoFA=1=to1activate ortwoFA=2to force in gateway.conf - The user logs in to
enableSparkView,it;a QR code appears
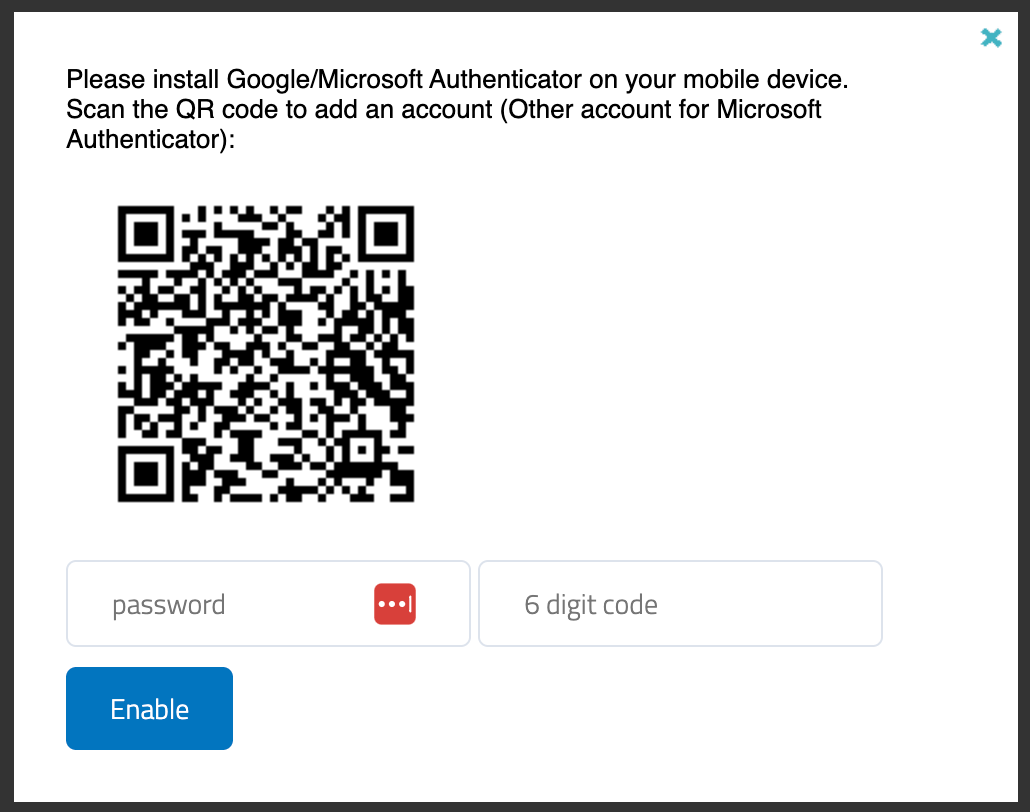
UserScanloginthe QR code withlogin.html,theaddAuthenticatoranappaccountand enter the 6-digit code
Reset second factor for individual users
There are 3 ways to reset the second factor for individual users:
Java-Command
To do this, the SparkView service must first be stopped. Then use the following command in the Settings:SparkView 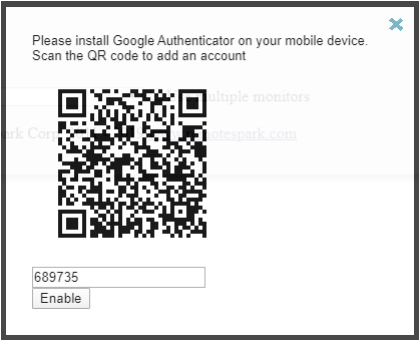
Delete the Two-factor authentication storage to reset for all users.Use the HTTP API to reset 2FA for a specific user. Please check theIntegration Guide (4.1)for more details.Command:directory:
sudo java -cp SparkGateway.jar com.toremote.gateway.tool.TwoFactor username(needFor
toADstopusers, please use thegatewayfollowingfirst).command:
sudo cURL-Request
The SparkView service must be running for this. Then please use the following command:
curl -k -G --data-urlencode "target=twofa" --data-urlencode "user=username" http://sparkview-server.com/CONTROL
For AD users, please use the following command:
curl -k -G --data-urlencode "target=twofa" --data-urlencode "user=domain\user.name" http://sparkview-server.com/CONTROL
HTTP request (API)
The SparkView service must be running and a hashed management password must be used. Then please call up the following URL:
http://sparkview-server.com/CONTROL?target=twofa&user=username&gatewayPwd=21232f297a57a5a743894a0e4a801fc3